Blog
Redis Service Management with requirepass AUTH enabled
Published: March 11, 2019
While reviewing a plan to introduce requirepass AUTH to a Redis instance prepared by a co-worker I came across the following note:
Will not set up init scripts, as starting/stopping Redis with AUTH directive enabled requires password
This didn’t smell right to me, so I decided to take a look at the issue with my co-worker.
Magento UI Component Magical Data Providers
Published: February 27, 2019
UI components are notoriously one of the most painful aspects of working with Magento 2.
I had some folks ask me about Magento 2's UI Component recently and realized everything I wrote about (now two years ago) has fled my head -- and I'm not sure I want to let it back in. https://t.co/Ubi9KVA1I0https://t.co/jtlTvuKEF9
— Alan Storm (@alanstorm) August 28, 2018
One aspect that’s thrown me for a loop is the “magical data providers”. For example, if you look at vendor/dotdigital/dotmailer-magento2-extension/view/adminhtml/ui_component/dotdigitalgroup_order_grid.xml you’ll see the following…
<dataSource name="order_report_grid_data_source">
<!--The data source-->
<argument name="dataProvider" xsi:type="configurableObject">
<argument name="class" xsi:type="string">Magento\Framework\View\Element\UiComponent\DataProvider\DataProvider</argument>
...
But how could the Magento\Framework\View\Element\UiComponent\DataProvider\DataProvider class be responsible for providing data to the order report grid?
On Magento Module Vulnerabilities
Published: February 7, 2019
The topic of Magento module security has been heating up. Here are just a few things that have happened recently:
- Willem de Groot, the leading researcher tracking malware infections amongst the global Magento install base reported that Magento modules are now the main source of security breaches for Magento sites.
- In collaboration with several security-minded individuals (myself included) Willem also published, magevulndb, a repository tracking vulnerabilities in commonly used Magento modules.
- The topic of Magento module security is slated for discussion at the DevExchange at the upcoming Magento Live AU conference. The effort is being spearheaded by ExtDN
I have some strong thoughts on the matter which I haven’t been shy about sharing in the past…
So I think a requirement that @ext_dn should impose is around proper disclosure of vulnerabilities in modules.
— Max Chadwick (@maxpchadwick) November 27, 2018
Here, I want to express them in long form.
FCGI_PARAMS FastCGI record format
Published: February 4, 2019
Recently I was trying update Gopherus’ FastCGI payload to clear PHP-FPM’s security.limit_extensions value. Using Wireshark I knew I needed to edit an FCGI_PARAMS record.
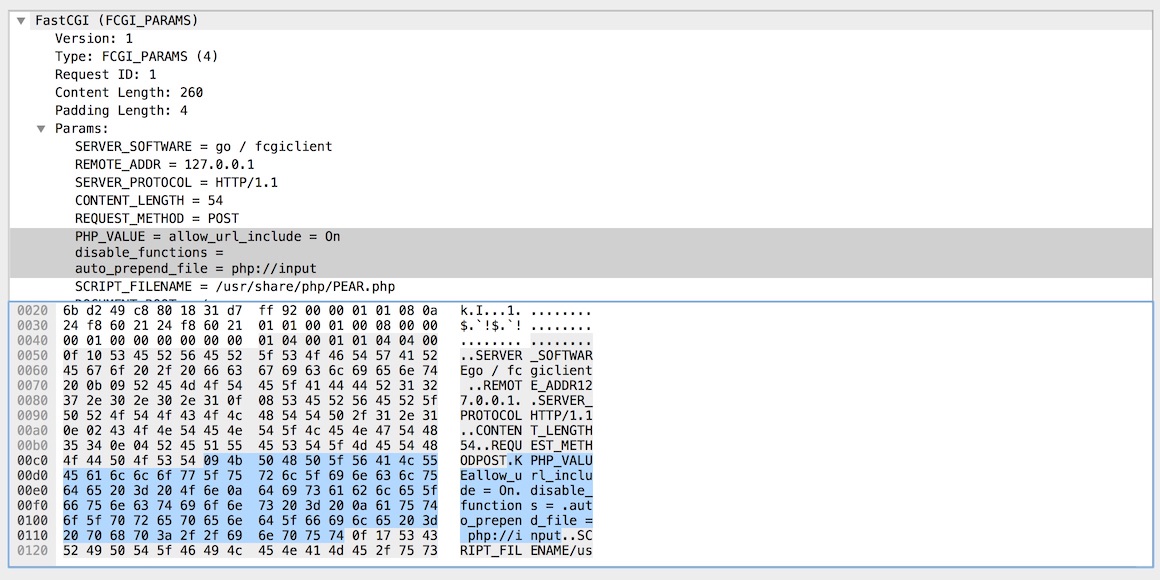
However, no matter how much time I spent with Google I couldn’t find a decent explanation of the format of a FCGI_PARAMS record.
Fortunately, after going through the a FCGI_PARAMS record byte-by-byte in Wireshark, I figured out what was going on. Here I’m documenting my findings for anyone else who finds them selves in the same shoes…
Inspecting FastCGI Packets with Wireshark
Published: January 30, 2019
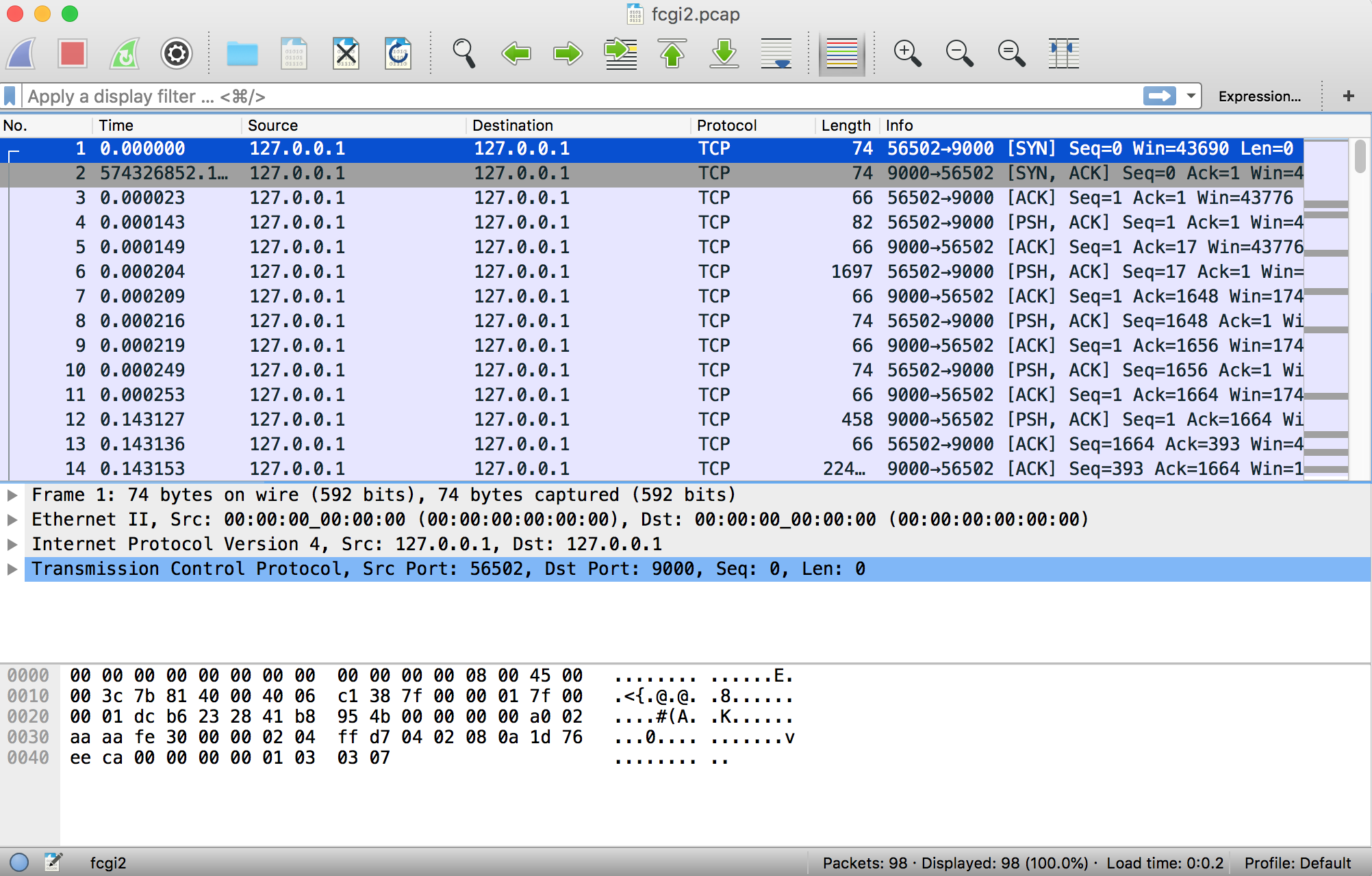
Recently I needed to do some analysis on FastCGI packets being sent to PHP-FPM.
Wireshark has a page on their wiki titled FastCGI which shows a screenshot of a pcap in Wireshark with detailed FastCGI info.
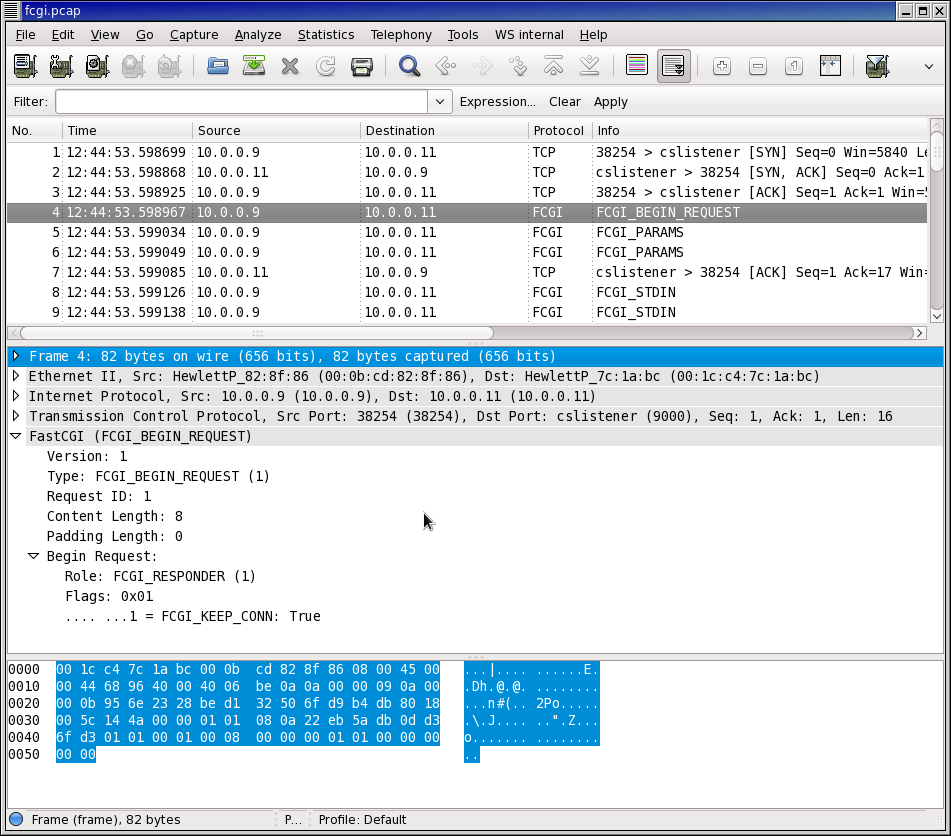
However, I couldn’t easily figure out from the wiki how to get the same details on my FastCGI pcap.
Xdebug Profiler Files Not In xdebug.profiler_output_dir
Published: January 17, 2019
Something that’s tripped up both myself and devs that I’ve worked with is not finding Xdebug profiler files in the expected directory (/tmp by default).
It usually goes something like this…
- Enable the Xdebug profiler by adding
xdebug.profiler_enable_trigger = 1to a.inifile. - Make a request with
?XDEBUG_PROFILE =1in the GET string. - Check for the output file in
/tmp - Pull out hair because it’s not there.
This may be accompanied by running a sanity check, only to be accompanied by more hair pulling…
$ php -r 'var_dump(ini_get("xdebug.profiler_output_dir"));'
string(4) "/tmp"