Blog
Linux Screen Cheatsheet
Published: April 25, 2018
There are a few of these, but none have all the answers that I want (e.g. how to scroll back up the terminal while attached to a screen session) or are in a format I like. So, I’ve prepared my own.
This is a cheatsheet of how to do the things I typically need to do with Linux (unix)’s screen command…
Exporting Your Browser Cookies on a Mac (Chrome, Firefox, Safari)
Published: April 12, 2018
Recently, for some research I’ve been doing I’ve had the desire to get an export of all my browser cookies. I wound up taking a look at how to do this the three browsers I use, Chrome, Firefox and Safari. In this post I’ll document my findings.
Magento + MySQL Query Cache: A Case Study
Published: April 1, 2018
The MySQL query cache is one of the most controversial MySQL features. While Percona concluded a blog post titled “The MySQL query cache: Worst enemy or best friend?” by stating that “the MySQL query cache is a good fit” for Magento, one of the world’s leading ecommerce platforms, the MySQL team announced that the query cache will be removed from MySQL 8.0.
On the Magento 1.14 Enterprise Edition site of a client I work with at Something Digital the query cache was inadvertently disabled, and later re-enabled once the issue was caught. This gave us great visibility into the impact the query cache was having on this application. Here I’ll share our findings…
Customers Seeing Wrong Order Confirmation Page / Customer Account In Magento
Published: March 18, 2018
Recently, I was looped in to the following issue reported by a client we recently onboarded at Something Digital…
Customers are placing orders and seeing the wrong order confirmation page. Also, customers are logging in and seeing the wrong customer account.
![]() Yes. It’s as scary as it sounds.
Yes. It’s as scary as it sounds.
This was a tricky one, but in the end I got to the bottom of it. Here, I’ll document the saga and solution.
New Relic's Overeager Browser Agent Injection
Published: March 9, 2018
NOTE: This post is based on the the New Relic PHP Agent as of Version 7.6.0.201
Recently I received a report from a client which read something like this…
Checkout is blocked on our website. Customers cannot place orders. Help!
I navigated to the website in question, added a product to my shopping cart and, upon clicking the “checkout” button was directed to a screen where I was prompted to select my “complimentary sample product”.
There, I selected a random “sample product” at which point a “loading” overlay appeared on the screen. I waited a few seconds and soon realized the overlay wasn’t going to disappear. I was effectively “blocked” from getting to checkout…
Digging in I found that the issue was caused by unencoded injection of the New Relic Browser Agent JavaScript into a JSON AJAX response leading to a JavaScript parse error, which prevented the overlay from disappearing and success message from showing up.
Here I’ll provide more details on the issue and my findings…
Images cannot be crawled because of robots.txt restriction: A Google Merchant Center Fallacy
Published: March 7, 2018
Recently at Something Digital I’ve been working with a client who’s been having a lot of trouble setting up Google Shopping ads.
After creating a product feed and submitting it to Google Merchant Center nearly half the products were listed as “Disapproved”. Drilling into these products in Google Merchant Center product details we saw the following error.
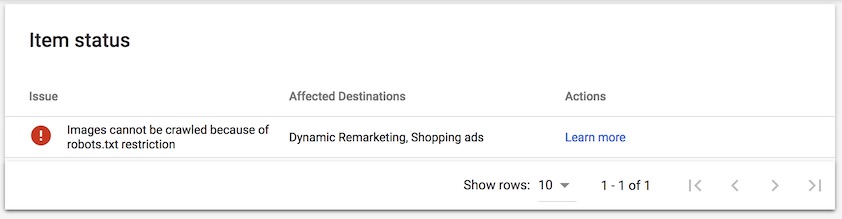
This stuck me as strange as, upon a quick check of the site’s robots.txt file I saw nothing that would prevent Googlebot from crawling the images in question.
We were ultimately able to resolve the issue, which, as suspected, had nothing to do with the robots.txt file. Here I’ll document my findings…